So after playing around for fun on Proxmox with IPSets trying to limit traffic being forwarded by geolocation to external facing services on one of my hosts I had to look for another solution. Unfortunately using allow and blocklists created through IPSet on a Proxmox cluster is.. well.. terrible and this type of filtering should really be happening as close to the ISP gateway as possible. That said, Proxmox only supports a cluster rule list of 128kb in size and this is hardly adequate for a world riddled with threat actors attempting to exploit any open ports on a network. Of course it is far more ideal to simply have an allow list and deny everything else which is accomplished fairly easily on a per country basis by using this awesome walk-through located here.
The reality is though, only allowing in traffic from countries IP address blocks using the above script still leaves an awful lot of potential source addresses for attacks to be performed that may actually occur from within the allowed country blocklist. I wanted to take this script and idea to the next level by doing the same thing for the emerging threats IP blocklist and the full tor node list from dan.me.uk.
I basically just made a couple small changes to the script originally used to generate a by country allow list to accomplish this. Further to this, I didn’t like the idea of having to install wget to download the IP lists as curl was already installed on the Edgerouter. As the walk-through above uses wget which was not natively installed on my Edgerouter and there was a warning from Ubiquiti regarding not to accidentally run an apt upgrade while doing the wget install process and altering repos to install wget located at https://help.ui.com/hc/en-us/articles/205202560-EdgeRouter-Add-Debian-Packages-to-EdgeOS, I figured it best, just in case to leave well enough alone and use curl as it was already installed. Less storage overhead too right?
In the article by Alex Jensen to set this up there are actually two ways to do the configuration preparation. The first is by following his command template on your Edgerouter in configure mode which is as follows:
set firewall group network-group countries_allowed description 'Allowed countries'
set firewall group network-group countries_allowed network 10.254.254.254/31
set service nat rule 10 description 'My funny dmz server'
set service nat rule 10 destination group address-group ADDRv4_eth0
set service nat rule 10 destination port 55555
set service nat rule 10 inbound-interface eth0
set service nat rule 10 inside-address address 192.168.xxx.xxx
set service nat rule 10 inside-address port 55555
set service nat rule 10 protocol tcp
set firewall name WAN_IN rule 20 action accept
set firewall name WAN_IN rule 20 description 'My funny dmz server'
set firewall name WAN_IN rule 20 destination port 55555
set firewall name WAN_IN rule 20 protocol tcp
set firewall name WAN_IN rule 20 source group network-group countries_allowed
commit
His explanation is:
This basically does the following:
- Creates a network-group that will be a placeholder for all the subnets I want to allow accessing my server. I add only one rule, that will be there when the Edgerouter is booted. That means that everything (except an arbitrary/random ip 10.254.254.254) is blocked until the real country-rules are loaded later.
- Then it makes a NAT forward rule that forwards all traffic to port 55555 coming in on my outside interface(eth0) to my internal server
- Allows the traffic to my server in the firewall if the traffic originates from my network-group “countries_allowed”
The second is by doing the same initial setup for everything while still executing the first two lines through the cli and then through this guide I found by Willie Howe at https://www.youtube.com/watch?v=7QSRNwFo6os. This is basically just setting up Destination NAT instead of port forwarding via the GUI. Another difference too is that you will have to apply the network group allow or block list through the GUI afterwords also to the rule.
Willie Howe also has a walk-through for the setup part of the above script by Alex Jensen that can be found at https://www.youtube.com/watch?v=Qn5hbdijYJM.
You would still need to run the first two commands for creating a firewall network group and assigning it an IP address place holder then using to commit to apply them before following the combination of the two Willie Howe video guides. (Just giving options, I prefer the CLI method myself).
The GUI doesn’t actually allow for you to enter a list of IPs into the firewall network group, thus it is done via command line. You must additionally be sure once the script has added and generated the list within the network group not to edit it in the GUI otherwise you will need to run the scripts again.
Anyways, the two additional scripts I added for specific use case scenarios and to additionally help filter out any known bad IP addresses within my country that may have snuck in on the allow list and any TOR nodes are as follows. (This is done once you’ve setup Destination NAT port forwarding.)
So to create the emerging threats blocklist, after I have setup Destination NAT port forwarding in the Edgerouter cli in configure mode run:
set firewall group network-group block_et description 'Block Emerging Threats' set firewall group network-group block_et network 10.254.254.254/31 commit
Create this script in the /config/scripts/post-config.d/ as block_et directory on the Edgerouter with 755 permissions. #chmod 755
#!/bin/bash firewallGroupName=block_et #mkdir /config/zonefiles function loadet () { firewallGroupName=$1 echo "Downloading country definition for $country..." >> /var/log/admin curl -O https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt sed -i /^#/d emerging-Block-IPs.txt sed -i '/^$/d' emerging-Block-IPs.txt mv emerging-Block-IPs.txt /config/zonefiles/emerging-Block-IPs.zone echo "Adding rules to firewall group $firewallGroupName..." >> /var/log/admin for rule in `cat /config/zonefiles/emerging-Block-IPs.zone`; do ipset add $firewallGroupName $rule done } ipset -F $firewallGroupName loadet $firewallGroupName
And for the Tor node list script:
set firewall group network-group block_et description ‘Block Emerging Threats’
set firewall group network-group block_et network 10.254.254.254/31
commit
Create this script in the /config/scripts/post-config.d/ as block_tor directory on the Edgerouter with 755 permissions. #chmod 755
#!/bin/bash firewallGroupName=block_tor #mkdir /config/zonefiles function loadtor () { firewallGroupName=$1 echo "Downloading fulltorlist definitions from dan.me.uk/torlist" >> /var/log/admin curl -0 https://www.dan.me.uk/torlist/ -o tl.txt sed -i /^#/d tl.txt sed -rn '/((1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])\.){3}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])/p' tl.txt > torlist.txt sed -i '/^$/d' torlist.txt mv torlist.txt /config/zonefiles/torlist.zone echo "Adding rules to firewall group $firewallGroupName..." >> /var/log/admin for rule in `cat /config/zonefiles/torlist.zone`; do ipset add $firewallGroupName $rule done } ipset -F $firewallGroupName loadtor $firewallGroupName
There are some extra commands in my scripts to clean them up and remove commented lines # and remove IPv6 addresses also since those are not applicable in my situation, that and if these lines aren’t cleaned up and formatted correctly they will fail to run.
Additionally to note is that the TOR node list from dan.me.uk is rate limited to one attempted download per 30 minutes so you may need to wait an additional 30 minutes if you’ve tried to run the script more than once, otherwise the file will be replaced by an error message and this won’t translate into a usable blocklist.
The scripts in this directory will automatically execute and update at a reboot or you could even setup a cronjob to run them and update while the system is on since it is unlikely rebooting your router is a regular occurrence.
You can run the scripts manually if you don’t want to reboot your Edgerouter.
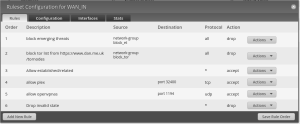
This is what my configuration looks like now on the Edgerouter as it is applied on WAN_IN.
In my case with the above screenshot since I actually have custom NAT rules to replace standard port forwarding giving me more control over ingress/egress traffic, my plex and openvpnas rules under WAN_IN are not exposed to all countries, they only accept traffic from IPSets specific to countries I have allowed as shown below in an excerpt from the NAT tab in the Firewall/NAT Menu of the Edgerouter gui.
Basically, everything into my network is dropped, but because there are allowed addresses into it, I want them to hit the block emerging threats/tor list first if they are within that list since the filter works its way down the list of rules until it finds a match to the incoming IP address.
Nothing like some automated security right? 🙂