A little privacy goes a long way whether it’s for simple web browsing or using Internet Relay Chat (IRC). Sure you can simply use a Virtual Private Network (VPN) to assist with anonymity, and there are plenty of those out there (I use Proton VPN), but there are certain use cases where using shared IP public or private VPN can result in bans from using services you wish to access anonymously because of other users malicious behavior. Not to mention it can be a little irritating to have all your outgoing traffic routed through a VPN client by default, and of course while routes are configurable, it can become a lot to manage when you are just looking to have a few services routed a certain way.
Enter SOCKS5 proxy – which basically routes designated* (I say designated because this is my use case) traffic through a proxy server. A proxy server is an intermediary connection between you and your destination and provides a layer of obfuscation at least as it relates to your geolocation via IP address. There are plenty of good articles already explaining SOCKS5 out there such as this one by makeuseof.com – so I will not go into further details with this.
What I wanted to do is have a designated, self hosted proxy server for random web browsing that won’t affect my ability to use my work VPN where I have several dozens of subnets being routed and to also run my IRC traffic through. This will help keep things organized for me.
In order to do this at least as I have it setup, you will need the following:
1 – Access to a Cloud Computing platform such as AWS, Azure or Linode to run a Virtual Machine to use as your proxy server.
2 – Dynamic DNS setup – as most of us do not have a static IP address, this will allow us to have an extra layer of security on our Virtual Private Server (VPS).
I will not be getting into the details of setting up Dynamic DNS but you can start here at no-ip.com for example to configure it. There are other options as well.
For my VPS setup I used a Linode Nanode with 1 CPU and 1 GB of Ram – which is more than enough resources for this task. I chose to use Ubuntu 22.04 LTS and would recommend using a Debian based operating system for this installation – specifically a version of Ubuntu given that the SOCKS platform Microsocks is already available for installation through apt.
Once sshed into your new VPS update and upgrade your distro.
Then sudo apt -y install microsocks to install microsocks SOCKS proxy.
Now I disabled UFW because I prefer to use iptables to manage my firewall.
sudo systemctl disable ufw –now
Run iptables -vL and you should see an empty set of tables with no rules.
There are three scripts we need to create. Two to manage the firewall and one to manage to Microsocks.
sudo mkdir -p /opt/iptables /opt/microsocks
The first script we will place in /opt/iptables and call it iptables.sh. Be sure to chmod +x this script so it can execute. This script will set iptables rules to limit incoming connections to your VPS to those on port 22 for SSH and port 1080 for SOCKS from your dynamic dns address (which will be your home IP address). Be sure to update your_dynamic_dns.address with your dynamic dns name.
#!/bin/bash #this only stores in memory not persistent iptables -F myip=$(dig your_dynamic_dns.address | grep your_dynamic_dns.address. | awk 'END{print}' | awk '{print $5}') #defaults ipv4 iptables -A INPUT -s $myip -p tcp --dport 22 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT iptables -A INPUT -s $myip -p tcp --dport 1080 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT iptables -A INPUT -i lo -j ACCEPT iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT iptables -P INPUT DROP iptables -P FORWARD DROP #defaults ipv6 - there aren't any specifically good blocklists for ipv6 so just going to leave it shutoff for anything but localhost ip6tables -A INPUT -i lo -j ACCEPT ip6tables -P INPUT DROP ip6tables -P FORWARD DROP
The second script will also be placed in /opt/iptables and we will call it updateiptables.sh. Be sure to chmod +x this script so it can execute. This script will simply update the iptables rules given that your dynamic home IP address changes for any given reason without you having to intervene on the VPS.
#!/bin/bash #this only stores in memory not persistent myip=$(dig your_dynamic_dns.address| grep your_dynamic_dns.address. | awk 'END{print}' | awk '{print $5}') #updates defaults ipv4 iptables -R INPUT 1 -s $myip -p tcp --dport 22 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT iptables -R INPUT 2 -s $myip -p tcp --dport 1080 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT
The third script will be placed in /opt/microsocks and we will name it microsocks.sh. Be sure to chmod +x this script so it can execute. This script will run the microsocks service and listen for incoming connections. By default it listens to 0.0.0.0 and on port 1080. You will need to specify a username and password. The -1 flag you see in the beginning will add the IP address to a whitelist so auth is not required later for that IP. Pick a strong username and a strong password. Use a password manager to store these credentials.
#!/bin/bash microsocks -1 -u PICK_A_USERNAME -P PICK_A_PASSWORD
Next we need to make two service files. One to load the initial iptables script and one to run the microsocks script. Yes you can run these as a cronjob there is nothing stopping you from doing that. I find this easier to manage things I want to be able to restart on the fly though.
Navigate to /etc/systemd/system. create ipscript.service and microsocks.service.
The contents of ipscript.service will be:
[Unit] Description=iptables service script After=network-online.target [Service] ExecStart=/opt/iptables/iptables.sh [Install] WantedBy=multi-user.target
The conents of microsocks.service will be:
[Unit] Description=microsocks service script After=network-online.target [Service] ExecStart=/opt/microsocks/microsocks.sh [Install] WantedBy=multi-user.target
Then run the following commands: sudo systemctl daemon-reload sudo systemctl enable ipscript --now sudo systemctl enable microsocks --now
This will reload these services, and start and enable them immediately.
The iptables script will essentially run on startup only and load those rules into the filter table. The microsocks service will be continually running in the background listening for connections.
The third script – this is where we will use a cronjob to schedule it to run every 60 minutes to check for a dynamic dns record update. You can customize this interval though to any value you wish.
sudo crontab -e
Add this to the end of the file
#update iptables 0 * * * * /opt/ipsets/updateiptables.sh
This will now run the updateiptables.sh script and replace the values in the filter table if there was an update, to only allow connections in from your home address. Please feel free to make the interval faster if you are worried about your service provider causing quick and random dynamic IP address updates.
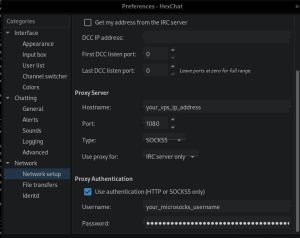
Now lets test it out. I use HexChat for IRC. Update the information in the HexChat preference tabs and click okay.
You should now be connected to IRC using your very own personal SOCKS proxy. The nice thing is, since you have authenticated this way – if you were to set your web browser to use your VPS proxy, you won’t need to enter credentials for your current IP address, as its now been authenticated and whitelisted from the initial IRC connection.
You will now have a VPS SOCKS proxy that only accepts incoming connections from your home network and that will not be shared with anyone else.
Though this doesn’t prevent someone from knowing your proxy IP address, it helps to create an additional layer of protection to ensure you are keeping anonymous. You could also setup multiple users and share with your friends! Though, don’t go spying on their traffic.